This blog originally appeared in October 2020 on the Area 1 Security website, and was issued in advance of Cloudflare's acquisition of Area 1 Security on April 1, 2022. Learn more.
Mark your calendars, October 13-14 is Amazon’s Prime Day! A whole 24 hours of exclusive deals just for Prime members. For most of us who haven’t been impulsively buying during the quarantine after spending all day sitting on our laptops, this means it might be time to open up Amazon and check out the latest deals.
However, cyber criminals have also prepared for what may likely be the biggest Prime Day ever. Each year, they ramp up their Amazon phishing schemes, to steal login credentials and credit card details with convincing lures regarding Prime membership.
Amazon is a highly spoofed company. Criminals commonly use Amazon to steal sensitive information as a means to bolster their ill-gotten coffers. Targets can be easily tricked by these phishing messages as attackers continually update to more and more timely and convincing lures.
Coronavirus-related lockdowns, combined with Prime Day sales, gives cyber criminals the ideal scenario for criminal activity. Instead of perusing shopping aisles with limited capacity and reduced hours, customers rely more than ever on Amazon for daily necessities and now, of course, the highly-anticipated Prime Day deals.
What else makes Prime Day risky in 2020? Many big box retailers cancelling their Black Friday sales in light of the pandemic. This makes Prime Day an even bigger focus for cyber criminals.
This year, attackers are using several advanced tactics to create more convincing messages.
Your Amazon Account’s On Hold - Update Payment Info
Amazon shoppers should understand the latest methods employed by cyber criminals, in order to avoid falling victim to these types of scams.
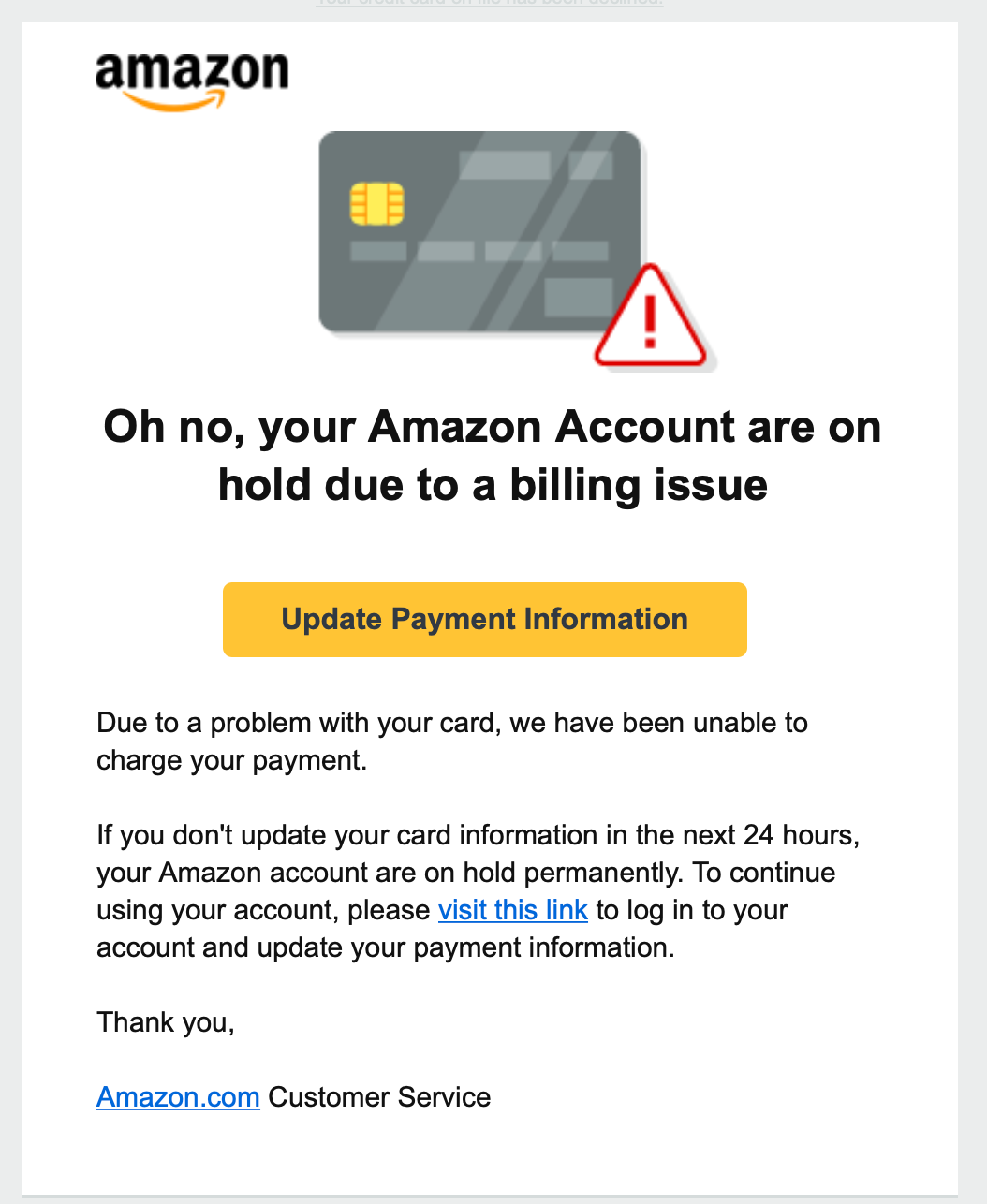
Here is the most prevalent phishing lure uncovered by Area 1 Security researchers: An Amazon-branded email states that there is a problem with the credit card linked to the user’s Amazon account, and the customer’s account is “on hold” until the customer can provide updated card information.
This scam, of course, is just an attempt to steal an Amazon Prime member’s credit card data.
We’ve found a number of disparate campaigns leveraging similar lures but with varying levels of sophistication.
The more stealthy phishing messages reveal convincing brand-specific content, carefully constructed to imitate a real Amazon email.
As shown in Figure 1, the content, logo and graphics are in line with what you might encounter in an actual Amazon notification email. The attacker behind this campaign used several advanced tactics to create a convincing message, including:
- Meticulous HTML/CSS coding
- Embedding images from Amazon in the source code
- Hosting malicious content on a legitimate website
- Leveraging Newly Registered Domains (NRDs) to send the phishing messages
This particular campaign used numerous domains to send their phishing messages, all of which were newly registered. The sender email accounts containing these domains followed either one of two patterns:
- no-reply-amazon-notify<11 alphanumeric characters>@<newly registered domain>
- mail-services-amazon-prime-<11 alphanumeric characters>@<newly registered domain>
The phishing messages sent from these accounts contained malicious links that revealed the attacker either leveraged NRDs, or abused the legitimate services of Sniply to host their Amazon look-alike sites.
What is Sniply? It allows users to create custom links with a free user account. As a result, Sniply is an attractive option for attackers looking to find unsuspecting sites to host their nefarious content.
The text “Update Payment Information” in the body of the message is a hyperlink to a presumably spoofed Amazon login page. Area 1 Security observed yet another pattern, this time with the Sniply links:
- hxxps://snip[.]ly/xjey66?.amazon-prime-services=
- hxxps://snip[.]ly/o1u9cb?amazon.data.prime=
- hxxps://snip[.]ly/9axm0u?ad-amazon.isuue-id=
The identification of these patterns in both the sender addresses and malicious links is highly suggestive of a phishing kit.
At the time of our analysis, the pages for these links were no longer accessible. Fortunately, Sniply was quick to the draw and blocked access to the attacker’s malicious content. However, with attackers easily creating Newly Registered Domains, it won’t take long to create a new malicious website and begin another wave of phishing messages.
These ever-evolving Amazon-themed campaigns are an ongoing threat to many individuals and businesses alike. The use of NRDs, as well as abuse of legitimate services, make these phish particularly difficult to detect.
To make matters worse, because the URLs used in the attacks point to legitimate domains and the messages contain no malicious payloads, traditional defenses will continually miss phish like this.
Although we recognized and stopped this campaign from reaching users’ inboxes before any damage could be done, there are still similar and ongoing campaigns with active links that are hitting the inboxes of targets without adequate email security.
As malicious actors create new campaigns with increasingly sophisticated tactics, users need to be aware of the latest techniques to stay safe from these opportunistic attacks.
Your Amazon Prime Membership Has Expired
Another Amazon-themed phishing campaign, launched in the days leading up to Prime Day, attempts to convince shoppers that their Prime membership has expired.
This campaign entices the customer to click a link to update card information on file in order to continue enjoying their Prime benefits. In the figure below, you can see that the message is simple, to the point, and — again — contains Amazon branding.
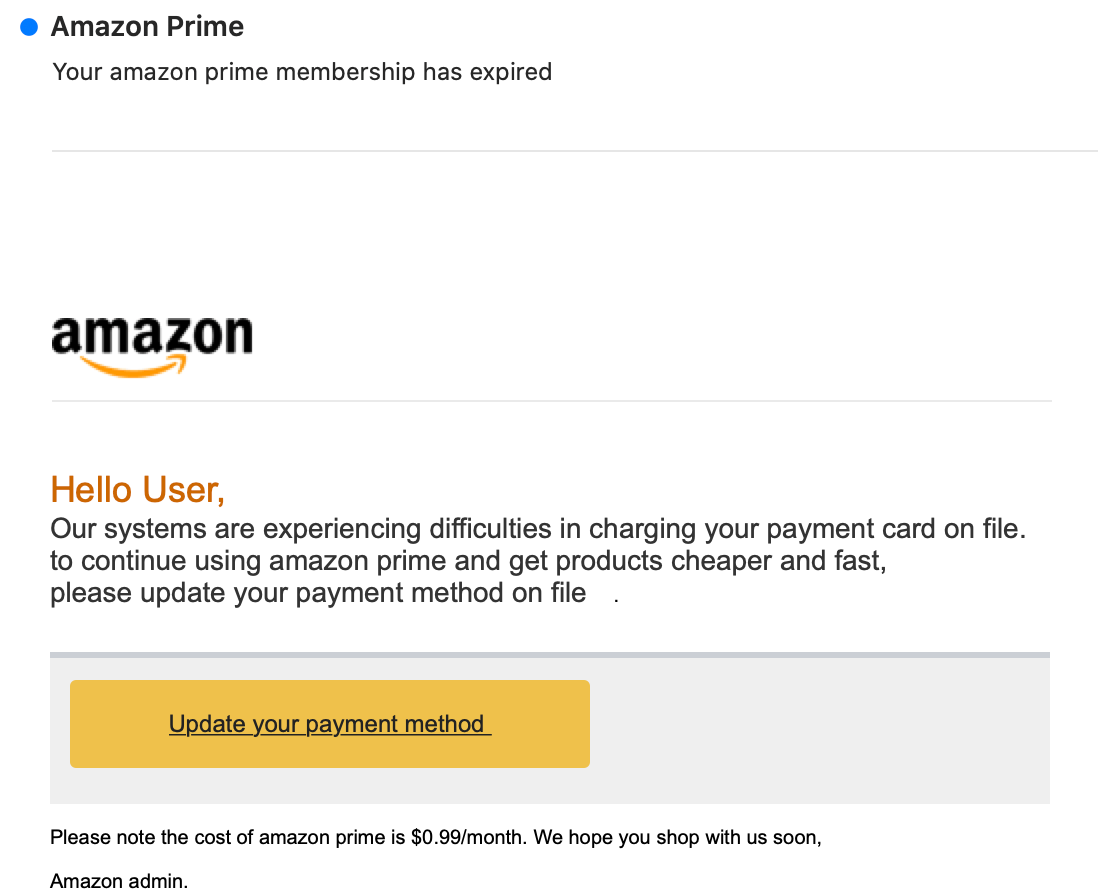
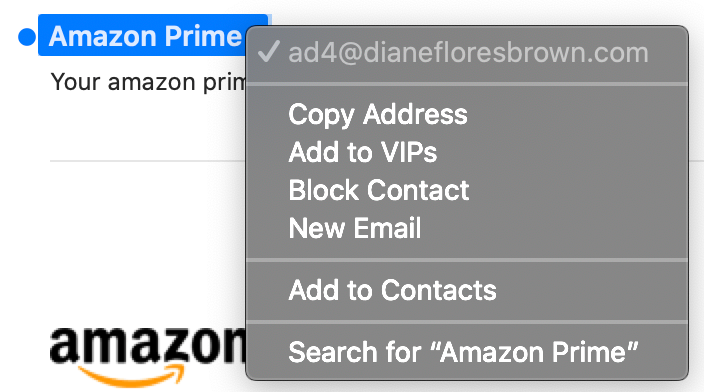
In the example above, the fraudsters used Display Name Spoofing to make the email appear as if it originated from “Amazon Prime”.
However, Area 1 Security’s closer inspection of the email headers reveals that the message has an “envelope-from” address of ad4@dianefloresbrown[.]com and was sent by way of wineu[.]mail.
At the time of analysis, these domains did not resolve to any IP addresses. Further, all IPs appearing in the header were private (or for internal network use only), having no significance outside the local network, and thus providing some degree of anonymity for the attacker.
This particular campaign has been linked to malicious Amazon-related spoofs dating back to 2016, and is still being updated on an almost daily basis.
A number of the phishing websites used by this cyber criminal happen to share a unique URL pattern, allowing for easier tracking of the fraudulent activity.
For example, clicking on the hyperlink for the text “Update your payment method” will result in the victim’s browser loading the malicious content located at, hxxps://asxtbibcx[.]com/amazon/ama/ACCESS744558886441BNG5F7558DERS85699SVB/F92a1dd58f9544ab8efd1c744612385a9/?dispatch=KNE0iodoOoqK5tDxLF7q0bbIsyFnO28x2xuq3Qvu5sVyxSL3EE. In an effort to avoid detection and being indexed by various web crawlers, every time the link is clicked, a new URL is generated. Parameters within the URL that vary are detailed below:
- hxxps://asxtbibcx[.]com/amazon/ama/ACCESS744558886441BNG5F7558DERS85699SVB/F<hashed and base64-encoded GMT/UTC timestamp>/?dispatch=<randomly generated alphanumeric characters>
After clicking the malicious link, the victim is directed through a series of steps to verify their identity and input payment information. Before being redirected to the real Amazon site, the victim is presented with a screen that displays their account has been successfully updated, and they will be logged out.
The figure below exposes the victim’s journey across multiple Amazon-branded sites:
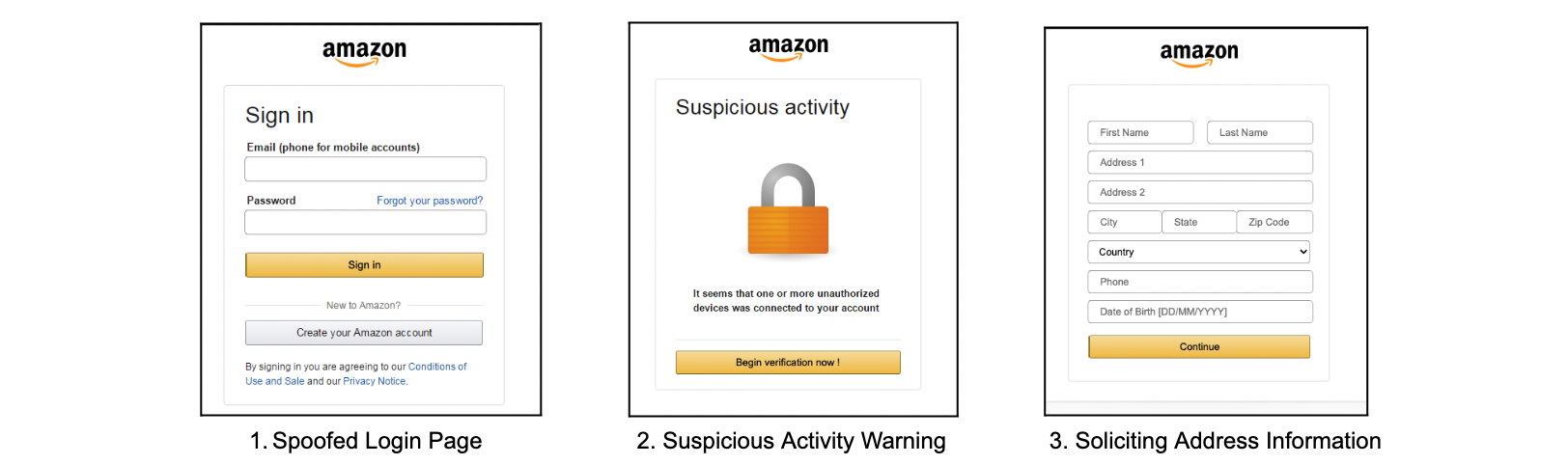
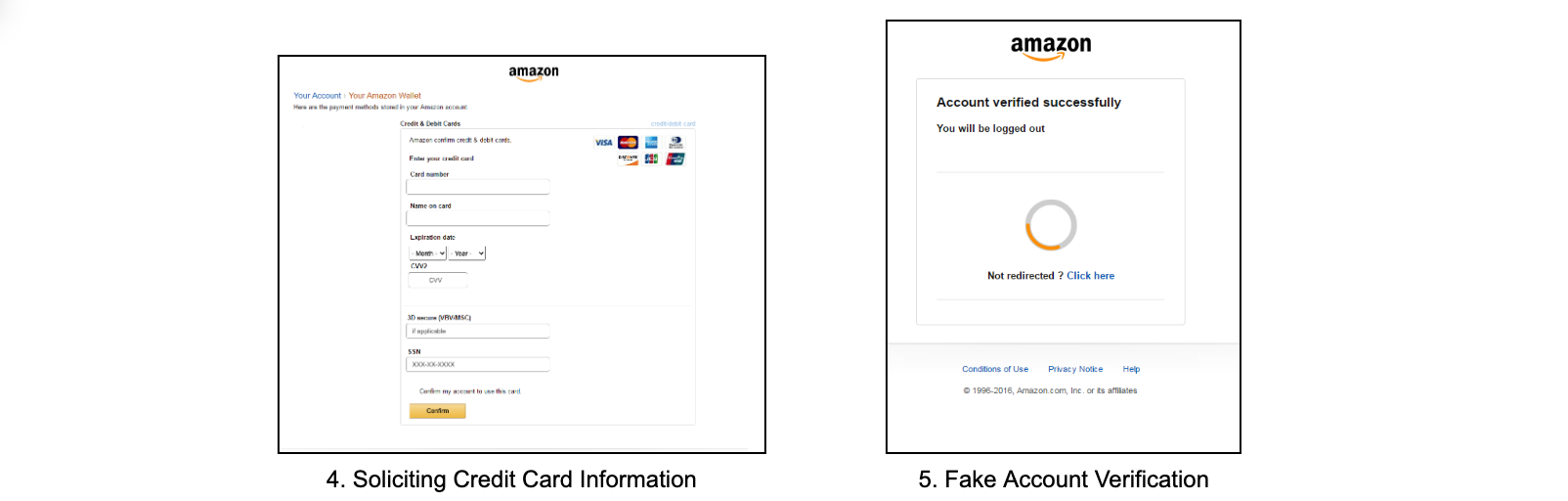
As evidenced above, the attacker is attempting to steal not only credit card, but also personally identifying information (PII).
This sensitive data is then sent to the attacker at the addresses btsmpil@gmail[.]com and kabiyesi@zoho[.]com. There are no cookies stored once the target is redirected to the Amazon homepage, indicating that the attack does not attempt to get additional information from the Amazon session.
In a misstep by the attacker, the index of their malicious website was made public (as shown in Figure 5), allowing anyone to view the technical details behind their operation.
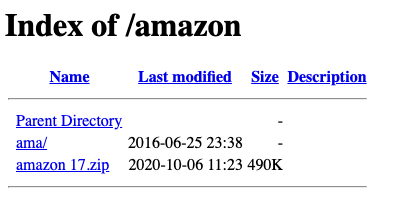
This oversight allowed researchers at Area 1 Security to access the source code for the website and delve into the numerous scripts used to carry out the attack.
Several unique artifacts were discovered that can be used to possibly identify any additional or future campaigns carried out by this attacker. For instance, a number of div classes follow a very similar format:
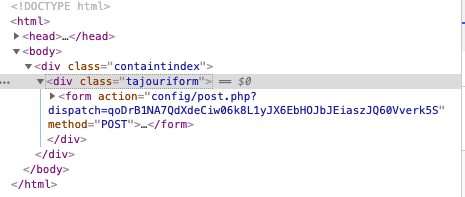
As revealed in the figure above, each of the div classes uses “tajouri” as a prefix for containers, as well as the name of “containtindex”. No information was found as to why this was used as a naming convention, however it might give researchers another possible avenue for associating this cyber criminal with future attacks or phishing kits.
The main index page for the malicious site contains the code responsible for safeguarding its contents from web crawlers and for generating unique URLs for each visitor. As highlighted below, a screen name was identified on this page, “AYB SCH”, among a trove of profanity-laced code. Whether this attacker wanted the code to be discovered in order to gain internet notoriety is up for debate.
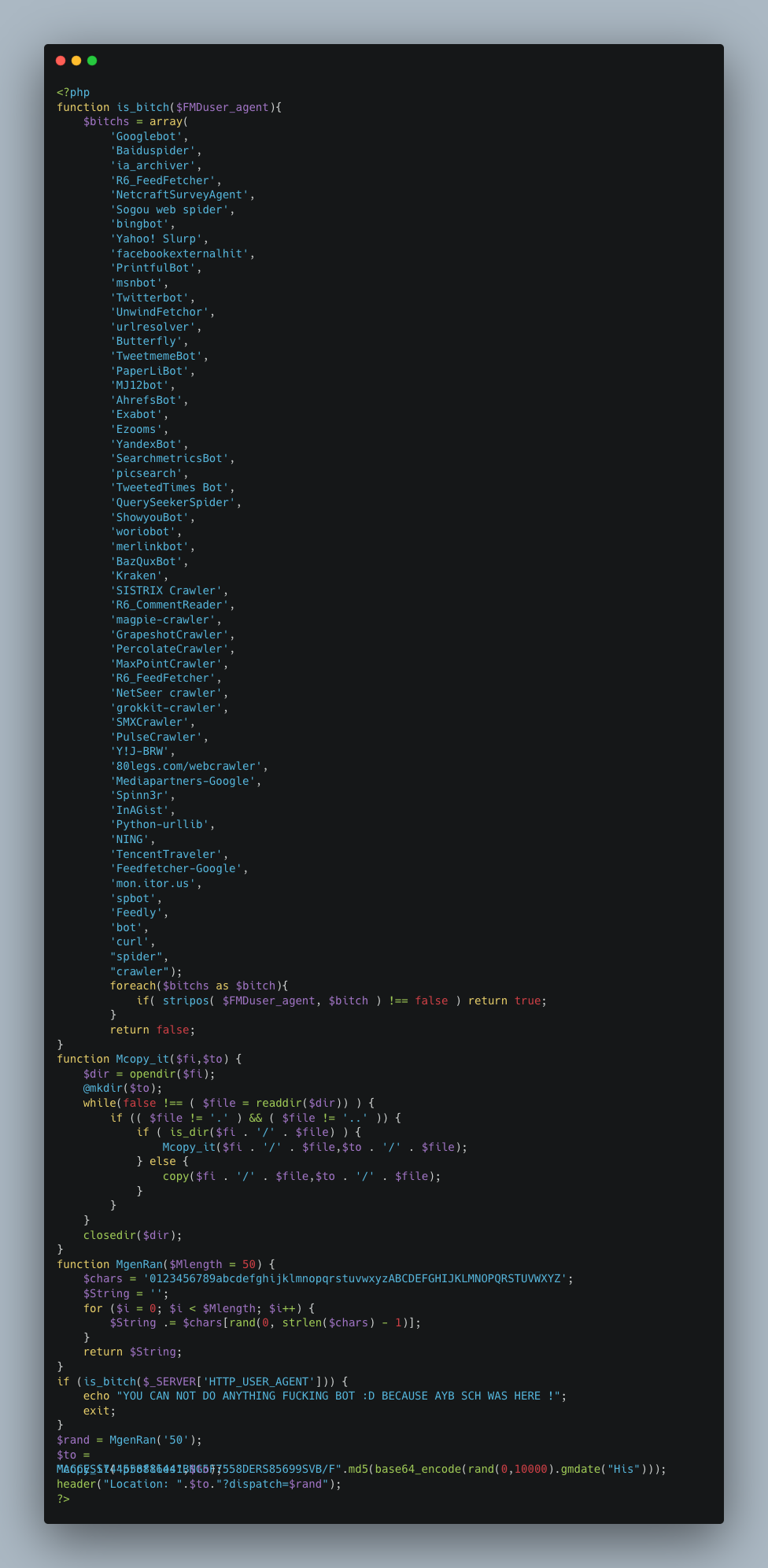
An additional artifact was found that offers yet another interesting, if not unique, identifier used by this cyber criminal. The below code comes from the “Account Verification” step of the attack. The specific div class format can be seen once again, as well as what appears to be French text in the HTML’s <p> tags, which is slang for “shut up”.
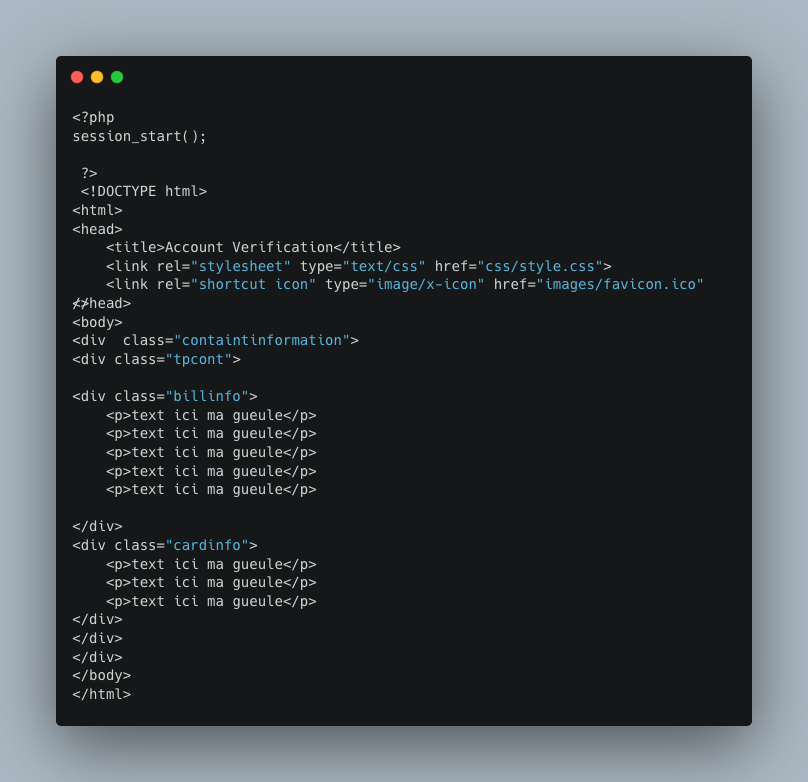
This source code provides a little insight into the cyber criminals behind these Amazon-themed attacks.
Many of the phishing campaigns appear to originate from overseas, as seen in the ISPs used, and were orchestrated by individuals who are well-versed in programming, if not English expletives. These fraudsters clearly see this as a game, where they hope to outsmart defenses while taunting those that may be hot on their trail.
Recommendations
With cyber criminals well-equipped for the upcoming rush to Prime Day deals, it is vital that companies prepare adequate defenses to protect users from falling victim to these Amazon-themed attacks.
As malicious actors invent new ways to bypass defenses, including the use of newly registered domains and legitimate online services, security practitioners need to turn to solutions on the cutting edge of email security technology in order to block these highly-damaging, financially-driven phishing campaigns.
New tactics and methods may be able to trick legacy vendors and cloud email providers, but Area 1 Security’s anti-phishing solution stops these fraudsters dead in their tracks.
Our advanced Machine Learning and Artificial Intelligence technology allows our algorithms to uncover new tactics malicious actors are using to bypass defenses in real time versus waiting days or weeks for signature updates. Our time-zero detections lead the industry with reliable verdicts that stop phishing attempts at delivery time. This has many advantages over post-delivery retraction in that users are never exposed to the attack.
Indicators of Compromise
Sender Domains:
Kimakxbisakok[.]com
kauadalahmantanterinda[.]com
Ikannilakayarasa[.]com
Bilangbabiamadia[.]com
com-accountingproved.com
ad4@dianefloresbrown[.]com
wineu[.]mail
Sender IP Addresses:
36[.]71[.]143[.]138
36[.]68[.]138[.]85
Sender Email Addresses:
no-reply-amazon-notify5jsciki79he@kimakxbisakok[.]com
no-reply-amazon-notify1os6uge0kzh@kimakxbisakok[.]com
no-reply-amazon-notifyhrbdqdoupsz@kauadalahmantanterinda[.]com
no-reply-amazon-notifym55jh93ft92@kauadalahmantanterinda[.]com
no-reply-amazon-notifykf9ul2d33jx@ikannilakayarasa[.]com
no-reply-amazon-notifymn5dzrjbwwc@bilangbabiamadia[.]com
mail-services-amazon-prime-pswrpeavczy@com-accountingproved[.]com
mail-services-amazon-prime-2av302jgvrp@com-accountingproved[.]com
mail-services-amazon-prime-5yww41luv8a@com-accountingproved[.]com
mail-services-amazon-prime-i7a98af4a29@com-accountingproved[.]com
mail-services-amazon-prime-xroq3gqfnm3@com-accountingproved[.]com
Attacker Email Addresses:
btsmpil@gmail[.]com
kabiyesi@zoho[.]com
Malicious Links:
hxxps://snip[.]ly/xjey66?.amazon-prime-services=<redacted>
hxxps://snip[.]ly/o1u9cb?amazon.data.prime=<redacted>
hxxps://snip[.]ly/9axm0u?ad-amazon.isuue-id=<redacted>
hxxps://interistingkostins[.]com/MwM7tEjhxxps://asxtbibcx[.]com/amazon/ama/ACCESS744558886441BNG5F7558DERS85699SVB/F<hashed and base64 encoded GMT/UTC timestamp>/?dispatch=<randomly generated alphanumeric characters>

