Microsoft 365
Deliver a faster and more secure user experience with Microsoft and Cloudflare

Cloudflare Email Security deploys and integrates in minutes with Office 365 to seal its protection profile with a preemptive, comprehensive, and accountable defense from socially engineered phish. The anti-phishing capabilities of Cloudflare Email Security fit tightly with the email security features included in Office 365, including anti-spam, DLP, encryption, and archive to provide total, seamless email security against phishing attacks.
Cloudflare has also become a certified partner in the Microsoft Networking Partner Program (NPP) for Microsoft 365. Microsoft has designed this program to offer customers a select set of partners whose deployment practices and guidance are aligned with Microsoft’s networking recommendations for Microsoft 365 to provide users a fast and secure user experience.

Integrated Email Security
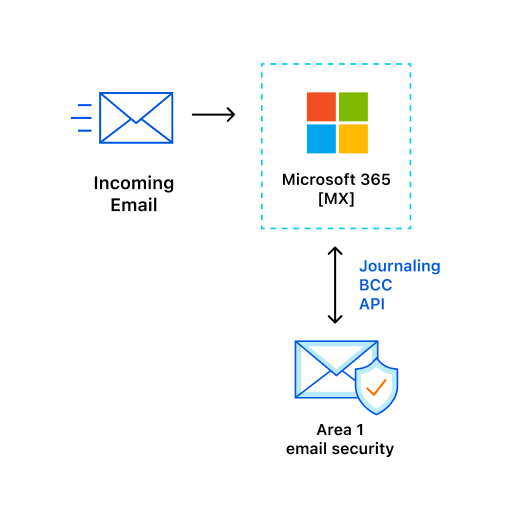
Cloudflare Email Security proactively crawls the web to discover phishing campaigns and uses that early insight, plus contextual email analysis techniques, to protect employee inboxes from phishing attacks — before damage can occur. Deploy Cloudflare Email Security in just minutes for a best-of-breed, defense-in-depth anti-phishing security layer for your Microsoft 365 email users.

Cloudflare One simplifies administration, improves control, and increases visibility
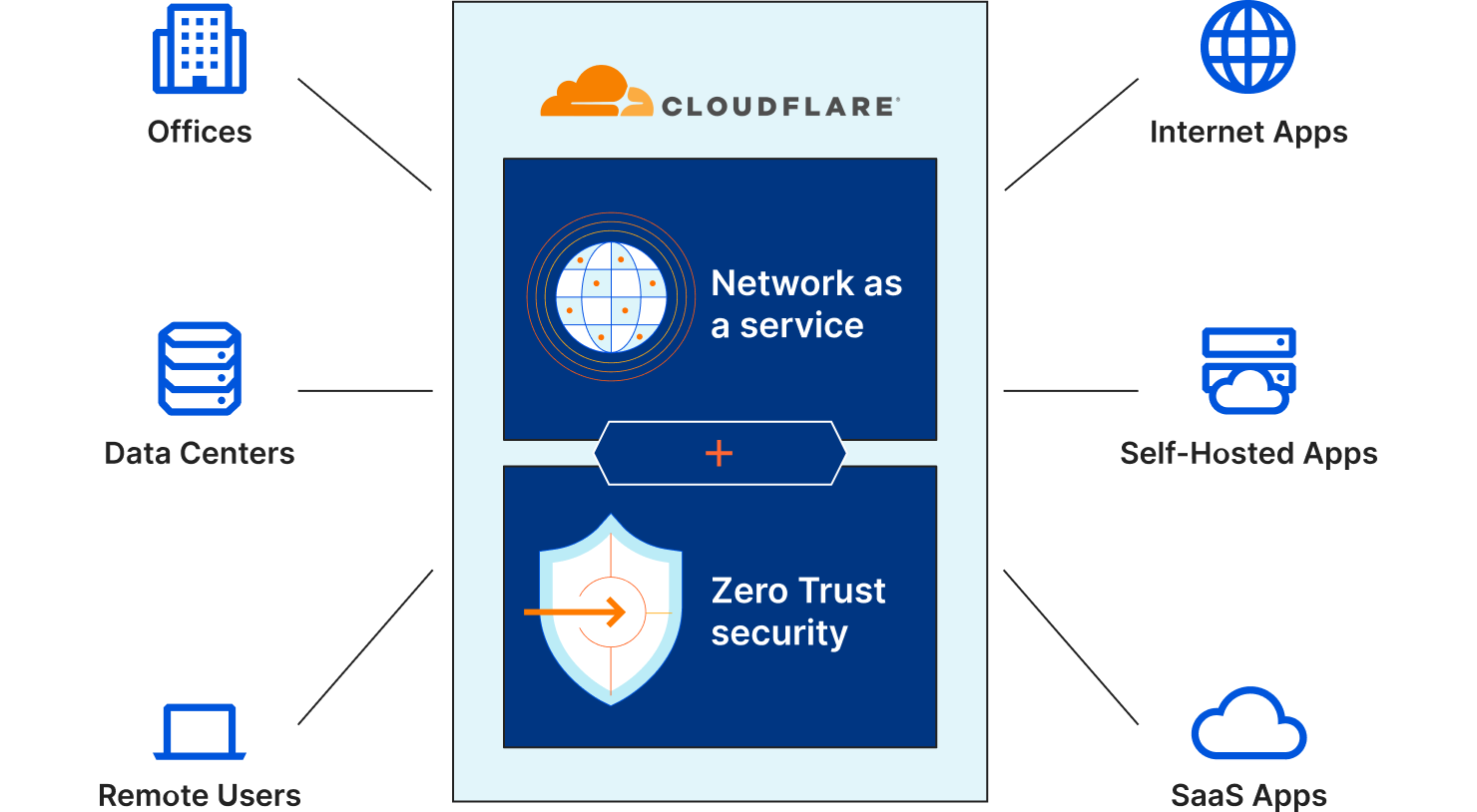
Keeping up with Microsoft’s continuous IP and URL changes can be daunting, and missing an update can adversely impact the user experience. Cloudflare One simplifies administration by making Office 365 as easy as a 1-click checkbox.

Cloudflare peers with Microsoft in major data centers
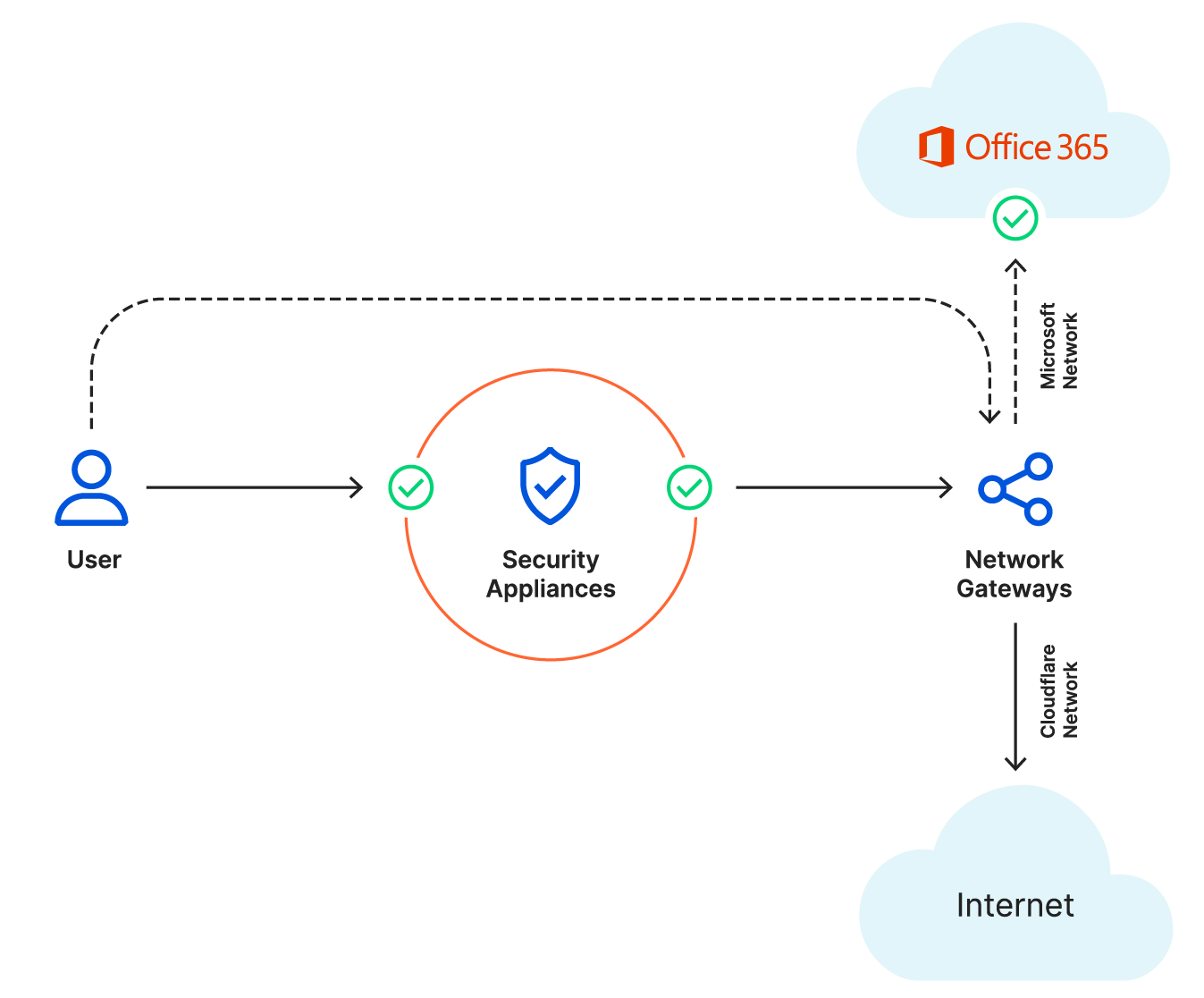
Delivering extremely fast connection times between the user and Office 365 applications, Cloudflare’s network spans across 275+ cities and peers with Microsoft around the world with 7 private interconnects and 113 Internet exchanges with private/public peering.

If you're interested in learning more about our partner integrations with Microsoft, please get in touch.
Learn More
Secure Hybrid Work with Microsoft + Cloudflare
In this solution brief, learn about Cloudflare's integrations (CES, ZTNA, CASB, DLP) with Microsoft and how layering a Zero Trust approach can enhance your Microsoft security.
How to replace your email gateway with Cloudflare Cloud Email Security
Learn how the Cloudflare Cloud Email Security (formerly called Area 1) anti-phishing service complements Microsoft 365’s security features.
Microsoft 365 + Cloudflare Cloud Email Security Partner Brief
Learn how Cloudflare Cloud Email Security can augment Microsoft's existing defenses and protects against phishing campaigns of all types, from all sources, and across all potential attack vectors.
Deploying Cloudflare Cloud Email Security
Learn about customers’ different deployment architectures for Cloudflare Cloud Email Security (formerly called Area 1).
Microsoft + Cloudflare Cloud Email Security Documentation
Learn how Cloudflare Cloud Email Security integrates with Microsoft 365 to detect and block targeted phishing attacks.
Cloudflare announces participation in Microsoft's NPP
Read about how Cloudflare One helps optimize user connectivity to Microsoft 365 with the Networking Partner Program (NPP).
Microsoft 365 Networking Partners
Learn more about how Microsoft’s networking partner program helps customers achieve end-to-end connectivity through the most optimized route possible.
Cloudflare and Microsoft NPP Partner Brief
Learn how Cloudflare Zero Trust supports Microsoft�’s connectivity guidance to deliver a faster, more secure user experience.
Cloudflare Joins Microsoft 365 Networking Partner Program
Find out how NPP deepens the relationship between Cloudflare and Microsoft in the Zero Trust market.
Managing Clouds - Cloudflare CASB and our not so secret plan for what’s next
Learn about how Cloudflare's CASB integration with Microsoft 365 enables organizations to grant permissions and connect SaaS applications (via API) to CASB for security scanning and management.
Announcing Gateway + CASB
Learn how Cloudflare's API-driven Cloud Access Security Broker (CASB) integrates with Microsoft 365 to help IT and security teams see what applications and services their users are logging into and how company data is being shared.